Modeling the Environment: Business Domains, Technology Groups, Archetypes, and Vignettes
Modeling the Environment: Business Domains, Technology Groups, Archetypes, and Vignettes
Each business or enterprise has different priorities, threat environments, and risk tolerance. This makes the development and
application of a standardized scoring mechanism difficult, because the
assumptions of the mechanism may not match those of the enterprise
that is applying the scoring.
CWRAF attempts to minimize this difficulty by allowing users to model environment-specific considerations within the framework. These
considerations are then reflected in the formulas that produce
customized CWSS scores, which can then be used to identify which
weaknesses are most important.
The environment-specific modeling dimension of CWRAF consists of the following major concepts:
|
Business Domain
|
A major function or service that includes the operations and
interactions of a broad range of networked capabilities or
organizations from the public and private sector; government and
military; commercial and nonprofit organizations; academia, etc., that
are enabled or controlled by software/IT and require some degree of
resilience and security in transactions or operations. Examples
include Finance, e-commerce, Public Health, Emergency Services,
telecommunications, etc.
| |
Technology Group
|
A collection of inter-related, similar technologies that together
provide a set of features that are used to solve a class of problems,
possibly across a variety of domains. Examples of technology groups
include web technologies, embedded real-time systems, storage,
operating systems, etc.
| |
Technical Archetype
|
A general type of technical capability, component, system (or
system-of-systems), or architecture that is commonly used to support
the mission of a particular organization. Examples include a web
application, database, smartphone, SCADA, etc. An archetype may be
used within multiple business domains. For example, SCADA systems are
used in electrical power grids, manufacturing, oil and gas
transmission, and other domains; and many industries manage their
information using database-connected web servers.
| |
Vignette
|
A shareable, semi-formal description of a scenario that identifies a
set of connected archetypes that collectively perform a function
within a business domain.
| |
Business Value Context (BVC)
|
A description of the security-relevant assets and interfaces within an
individual vignette, combined with the security priorities of the
business domain. The BVC forms a bridge between the business domain's
security concerns and the technical impact of potential weaknesses
that are found within that domain.
| |
Technical Impact Scorecard
|
A list of the potential low-level effects of weakness exploitation
(e.g., code execution or system crash), along with the layers at which
exploitation could occur (e.g., application or network). Each
"technical impact" is given a subscore based on how the impact could
affect the performance of the business function outlined by the
vignette, in light of the security concerns as defined in the BVC.
The data from the Technical Impact Scorecard is then used to influence
the calculation of CWSS scores.
|
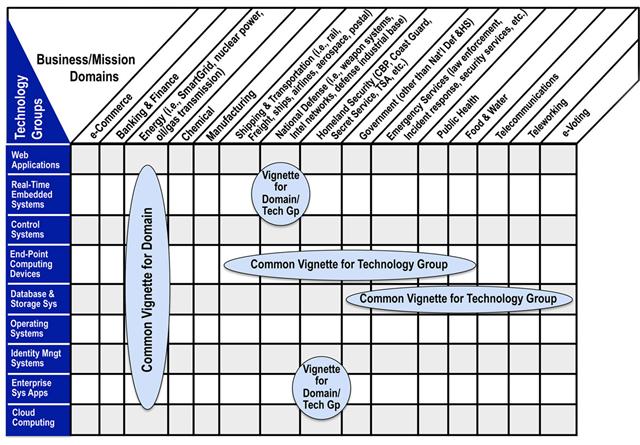
Technology Groups and Business Domains
The following table highlights the kinds of technology groups and business domains that are being investigated using CWRAF. Note that a
vignette can cross multiple domains (e.g., the use of end-point
computing devices in Shipping & Transportation, Public Health,
Homeland Security, etc.) A vignette can also utilize multiple
technology groups within a single domain such as Energy, in which the
Smart Grid uses many different groups.
An up-to-date version of this matrix highlights which vignettes have been defined and are under active
development.
Note: CWRAF users are not restricted to using such large-scale domains and technology groups. CWRAF can be customized
with user-defined domains, technology groups, and vignettes.
(A larger picture is available.)
Business Domains
Within CWRAF, a business domain typically covers a major industry or sector that includes the operations, processes, and interfaces for a
broad range of connected organizations, capabilities, or services that
are enabled or controlled by software and require some degree of
resilience and security in transactions and operations. Information
and communication technologies (ICT) cut across all domains.
Following is an example list of business domains. This list is being actively reviewed and modified. The
full, up-to-date list of domains is
provided in more detail on a separate page.
| Domain Name | Description |
|---|
|
e-Commerce
|
The use of the Internet or other computer networks for the sale of
products and services, typically using on-line capabilities.
| |
Banking & Finance
|
Financial services, including banks, stock exchanges, brokers,
investment companies, financial advisors, and government regulatory
agencies.
| |
Energy
|
Smart Grid (electrical network through a large region, using digital
technology for monitoring or control), nuclear power stations, oil and
gas transmission, etc.
| |
Chemical
|
Chemical processing and distribution, etc.
| |
Manufacturing
|
Plants and distribution channels, supply chain, etc.
| |
Shipping & Transportation
|
Aerospace systems (such as safety-critical ground aviation systems,
on-board avionics, etc), shipping systems, rail systems, etc.
| |
National Defense
|
Weapon systems, Intel networks, Defense Industrial Base, etc.
| |
Homeland Security
|
CBP, Coast Guard, Secret Service, TSA, etc.
| |
Government (Other)
|
Government (other than National Defense and Homeland Security)
| |
Emergency Services
|
Systems and services that support first responders, incident
management and response, law enforcement, and emergency services for
citizens, etc.
| |
Public Health
|
Health care, medical encoding and billing, patient information/data,
critical or emergency care, medical devices (implantable, partially
embedded, patient care), drug development and distribution, food
processing, clean water treatment and distribution (including dams and
processing facilities), etc.
| |
Food & Water
|
Food processing, clean water treatment and distribution (including
dams and processing facilities), etc.
| |
Telecommunications
|
Cellular services, land lines, VOIP, cable & fiber networks, etc.
| |
Teleworking
|
Support for employees to have remote access to internal business
networks and capabilities, e.g. networking-capable PDAs and cell
phones, VPNs, Network Access Control (NAC), Web-based email services,
etc.
| |
eVoting
|
Electronic voting systems, as used within state-run elections,
shareholder meetings, etc.
|
Technology Groups and Archetypes
Within CWRAF, a "technical archetype" is a class of technical capability, system (or system-of-systems), or architecture that is
commonly used to support the mission of an organization. Examples
include a web application, web server connected to a database;
Service-Oriented Architecture; Real-time, Embedded Device; end-point
computing devices (such as a Smartphone); process control system (such
as SCADA); etc. A technical archetype may be used within different
business domains. For example, SCADA systems are used in Energy,
Chemical, and other domains; and many industries manage their
information using database-connected web servers.
Technical archetypes can be used in multiple business domains, and certain archetypes may inherit certain classes of weaknesses. For
example, a web-based archetype may always have cross-site scripting
(XSS) as a concern. However, an archetype may have varying importance
depending on the business context. For example, a database archetype
that contains a retail customer's financial information and order
history may have different security concerns than a database that
contains sports statistics that are intended to be read by anyone.
Note that the definitions and usage of archetypes are still under review, and this concept may change in future versions of this paper.
They do not play an explicit role in CWRAF 0.8, although this may
change in future versions.
Following is an example list of archetypes categorized by their technology group. This list is being actively reviewed and modified.
The full, up-to-date list is provided
in more detail on a separate page.
| Technology Group | Archetypes/Description |
|---|
|
Web Applications
|
Web browser, web-server, web-based applications and services, etc.
| |
Industrial Control Systems
|
SCADA, process control system, etc.
| |
Real-time, Embedded Systems
|
Embedded Device, Programmable logic controller, implanted medical
devices, avionics package.
| |
End-point Computing Devices
|
Smart phone, laptop, personal digital assistant (PDA), and other
remote devices that leave the enterprise and/or connect remotely to
the enterprise.
| |
Cloud Computing
|
Hosted applications or capabilities provided over the Internet,
including Software-as-a-Service (SaaS), Platform-as-a-Service (PaaS),
and Infrastructure as a Service (IaaS).
| |
Operating Systems
|
General-purpose OS, virtualized OS, Real-time operating system (RTOS),
hypervisor, microkernel.
| |
Enterprise Desktop Applications/Systems
|
Office products such as word processing, spreadsheets, project
management, etc.
|
Vignettes
A vignette provides a shareable, formalized way to define a particular environment within a business domain. It includes the role that
software archetypes play within that environment, and an
organization's priorities with respect to software security. It
identifies essential resources and capabilities, as well as their
importance relative to security principles such as confidentiality,
integrity, and availability. For example, in an e-commerce context,
99.999% uptime may be a strong business requirement that drives the
interpretation of the severity of discovered weaknesses.
Vignettes allow CWRAF to support diverse audiences who may have different requirements for how to prioritize weaknesses. CWSS scoring
occurs within the context of a vignette.
Business Value Context (BVC)
An important part of a vignette is the Business Value Context (BVC). The BVC contains two main parts:
- (1) a general description of the security-relevant archetypes, assets, and interfaces that are of concern to the business domain
- (2) the security priorities of the business domain with respect to the potential outcomes that could occur if those archetypes are
successfully attacked.
Technical Impact Scorecard
A Technical Impact Scorecard connects the business concerns in the BVC with the possible technical impacts that could happen if an attacker
can successfully exploit the weakness, such as code execution, reading
of sensitive application data, or a software crash. For each
potential technical impact, the scorecard assigns a subscore and
provides a rationale for the assignment of the subscore. When a CWSS
score is calculated for a weakness, the data from the Technical Impact
Scorecard is used to influence the score to reflect the requirements
as described in the BVC.
Vignette Examples
A selection of example vignettes is presented below. These vignettes were selected to represent diverse communities and use cases. Note
that these vignettes are subject to change or removal based on
community review. A more extensive, up-to-date list of
vignettes is provided on a separate page.
Note that the Technical Impact Scorecard is omitted from this example for the sake of brevity; more details are available
in a later section.
| Domain | Vignette | Details |
|---|
|
E-Commerce
| Web-based Retail Provider
|
Internet-facing, E-commerce provider of retail goods or services.
Data-centric - Database containing PII, credit card numbers, and
inventory.
Archetypes: Database, Web client/server, General-purpose OS
BVC: Confidentiality essential from a
financial PII perspective, identity PII usually less important. PCI
compliance a factor. Security incidents might have organizational
impacts including financial loss, legal liability,
compliance/regulatory concerns, and reputation/brand damage.
| |
Banking & Finance
|
Financial Trading / Transactional
|
Financial trading system
supporting high-volume, high-speed transactions.
Archetypes: N-tier distributed, J2EE and supporting frameworks,
Transactional engine
BVC: High on integrity - transactions should
not be modified. Availability also very high - if system goes down,
financial trading can stop and critical transactions are not
processed.
| |
Public Health
|
Human Medical Devices
|
Medical devices - "implantable" or "partially embedded" in humans, as
well as usage in clinic or hospital environments ("patient care"
devices.) Includes items such as pacemakers, automatic drug delivery,
activity monitors. Control or monitoring of the device might be
performed by smartphones. The devices are not in a physically secured
environment.
Archetypes: Web-based monitoring and control, General-purpose OS,
Smartphone, Embedded Device
BVC: Power consumption and privacy a concern.
Key management important. Must balance ease-of-access during
emergency care with patient privacy and day-to-day security.
Availability is essential - failure of the device could lead to
illness or death. Devices are not in a physically secured
environment.
| |
Energy
|
Smart Meters
|
Meter within the Smart Grid that records electrical consumption and
communicates this information to the supplier on a regular basis.
Archetypes: Web Applications, Real-Time Embedded System, Process
Control System, End-point Computing Device
BVC: Confidentiality of customer energy usage
statistics is important - could be used for marketing or illegal
purposes. For example, hourly usage statistics could be useful for
monitoring activities. Integrity of metering data is important
because of the financial impact on stakeholders (consumers
manipulating energy costs). Availability typically is not needed for
real-time; other avenues exist if communications are disrupted (e.g.,
site visit).
| |
Teleworking
|
Remote Access Server
|
Remote Access Server used to support employees working outside the
enterprise, including teleworking/telecommuting.
Archetypes: Embedded Device, Endpoint System, Removable Storage Media,
Proprietary Firmware.
BVC: Strong authentication and authorization
is desired.
| |
Emergency Management
|
First responder
|
First responder (such as fire, police, and emergency medical
personnel) for a disaster or catastrophe.
Archetypes: End-point Computing Device
BVC: Communications and Continuity of
Operations (COOP) are essential, so availability is extremely
important. Integrity is needed to ensure that the correct data is
being used for decision-making and communications, such as status
updates and contact lists. Confidentiality is, relatively speaking,
less important.
| |
E-Voting
|
State Election Administration using DRE
|
State Election Administration using DRE (Direct Recording Election)
machines.
Archetypes: Embedded Device, Endpoint System, Removable Storage Media,
Proprietary Firmware
BVC: Integrity essential to election
terminals as well as endpoint systems used in pre-election device
programming. Protecting PII less important than ensuring accurate vote
tabulation and audit trails. Physical security of devices also
essential. Help America Vote Act (HAVA) requirements mandate paper
audit logs for use by election officials. Security incidents might
facilitate fraud via malicious influence of election process or
outcomes as well as incur Federal regulatory concerns, & erosion of
voter confidence.
| |
National Security
|
Weapon system sensor
|
Sensor for a weapons system that is connected to the Global
Information Grid (GIG).
Archetypes: Real-time Embedded System
BVC: Integrity is essential to prevent
reporting of false data and faulty decision-making. Lack of
availability could cause mission failure. Confidentiality may be
slightly less important.
|
In addition to a summary, each vignette is annotated with additional, lower-level details that can be used to describe how the technical
aspects of weaknesses relate to the business or mission-level
requirements. These details are discussed in another section.
Disclaimer: these vignettes are in the early stages of development and are intended primarily to demonstrate the concept. They are subject
to review and feedback, and they may be modified. An
up-to-date list of vignettes is on a separate
page.
Customizing CWRAF
Customizing CWRAF
Organizations can customize CWRAF to define their own domains, vignettes, etc. For example, an e-Commerce company could use Domains
to divide a software package into different processes, then use
vignettes to identify the most important functional components:
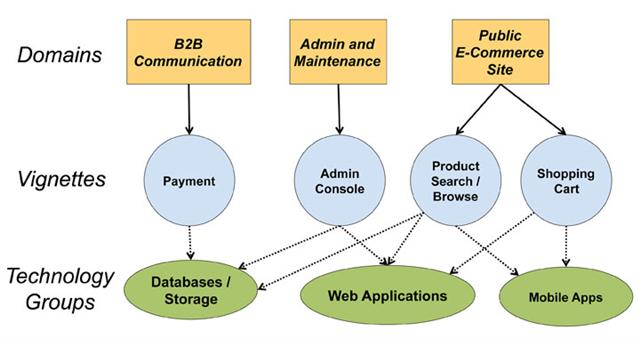
(A larger picture is available.)
More information is available — Please edit the custom filter or select a different filter.
|

