Introduction to CWRAF™
CWRAF provides a means for software developers and consumers to prioritize software weaknesses that are relevant for their business, mission, and deployed technologies. In certain circumstances, a software weakness can lead to an exploitable vulnerability. By providing a repeatable way to customize the Common Weakness Scoring System (CWSS™), CWRAF enables people to reason and communicate about the relative importance of different weaknesses. Users can automatically generate a more targeted specification of "Top-N" lists of weaknesses that are the most critical for the software that is used in the relevant business domains, missions, and technology groups. In conjunction with other activities, CWRAF ultimately helps developers and consumers to introduce more secure software into their operational environments. CWRAF provides a framework for scoring weaknesses in a consistent, flexible, open manner, that reflects the application's business context and what the application is doing for the business. It is a collaborative, community-based effort that is addressing the needs of its stakeholders across government, academia, and industry. CWRAF:
How to Use CWRAFCWRAF and CWSS allow users to rank classes of weaknesses independent of any particular software package, in order to prioritize them relative to each other (e.g., "buffer overflows are higher priority than memory leaks"). This approach, sometimes referred to as a "Top-N list," is used by the CWE/SANS Top 25, OWASP Top Ten, and similar efforts to provide measuring baselines for wide groups of industry to leverage in their own improvement activities. CWRAF and CWSS let users create top-n lists for their particular software and business domains, missions, and technology groups. In conjunction with other activities, CWSS and CWRAF help developers and consumers introduce more robust and resilient software into their operational environments.
CWRAF is designed to support stakeholder needs throughout the software lifecycle. However, the applicability of CWRAF extends beyond the design and development of software. CWRAF can be used to support Supply Chain Risk Management (SCRM) by giving software acquirers a means to define the software weaknesses that they deem most critical. CWRAF can also support the prioritization of training and education based on the unique needs of a business sector or organization. To be most effective, CWRAF supports multiple usage scenarios by different stakeholders who all have an interest in a consistent scoring system for prioritizing software weaknesses that could introduce risks to products, systems, networks and services. Some of the primary stakeholders considered in developing CWRAF are listed here. The high-level concepts in the Common Weakness Risk Analysis Framework are highlighted below. Complete technical details are provided below. 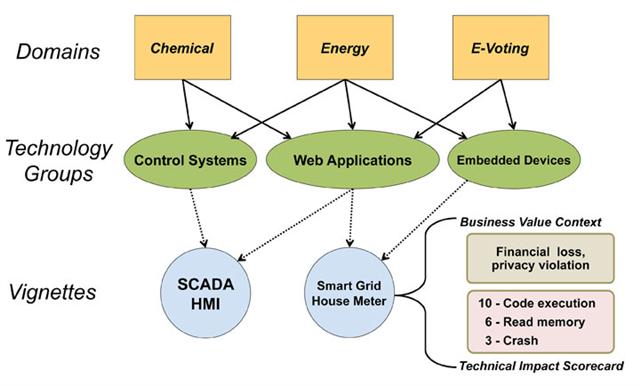 A "business domain" is a major function or service that includes the operations and interactions of a broad range of networked capabilities or organizations, such as Banking and Finance, Public Health, and e-Commerce. Within a business domain, a "vignette" provides a shareable, semi-formal description of a scenario that identifies a set of connected technology groups that collectively perform a function within a business domain. For example, a vignette in the e-Commerce domain may identify a retail-based web store that uses web applications and a database for customers to purchase various products and services. The underlying concept that CWRAF and CWSS leverage is that in spite of there being over 600 weaknesses in CWE, all of them lead to one or more of only eight (8) technical impacts when they manifest in the operational system. In other words, if a particular CWE in a piece of software is exploited when that software is in use supporting a particular business it will result in the attacker being able to: modify data, read data, create a denial-of-service that results in unreliable execution, create a denial-of-service that results in resource consumption, execute unauthorized code or commands, gain privileges / assume identity, bypass protection mechanism, and/or hide activities.
By exploring how important these various technical impacts are to the business that the application is supporting we can flow these “importance” ratings to the CWEs that can result in those technical impacts. As described above, the scoring of weaknesses in CWRAF and CWSS is directly influenced by the business domain in which the application runs and what it is doing to support that business, as well as the importance of the applications support to the business. The way CWSS scoring captures this business importance is by using the context of a vignette, which defines:
Using the Business Value Context and the Technical Impact Scorecard, CWRAF provides vignette-specific input to CWSS, which can then be used to prioritize which weaknesses are of greatest concern and ideally must be addressed first. Relationships between CWRAF, CWSS, and CWEThe following image summarizes the relationships between CWRAF, CWSS, and CWE: 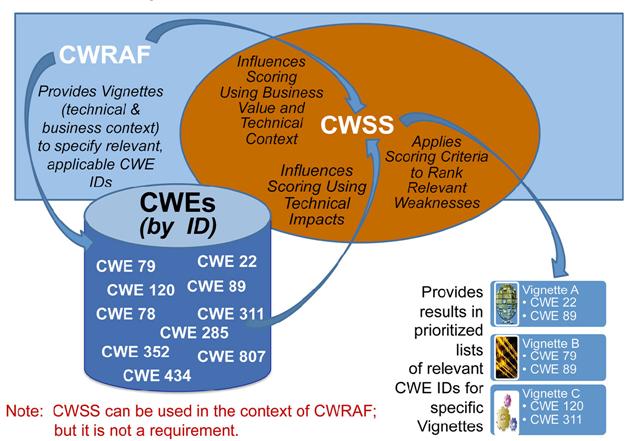
|
||||||||||||||||||||||||||||||||